Discover essential best practices for securing your cloud infrastructure in our ultimate guide. Protect your data and ensure robust security today!
As businesses shift to the cloud, security becomes a top priority. Cyber threats are rising, and weak security can lead to data breaches. Understanding the best practices for securing your cloud infrastructure helps you safeguard your assets. This guide will provide essential tips to protect your cloud environment.
From access control to monitoring, these practices ensure a robust defense. By following them, you can maintain a secure cloud infrastructure. So, let’s explore how to keep your cloud safe and secure.
Introduction To Cloud Security
Securing your cloud infrastructure involves following best practices like regular updates and strong access controls. Protecting data from breaches is vital. Implement encryption for sensitive information.
Securing your cloud infrastructure is essential in today’s digital age. Cloud security involves protecting data, applications, and services in the cloud. This ensures unauthorized users can’t access sensitive information.
Cloud security is a shared responsibility. Both the cloud provider and the user play roles. Providers offer tools and services to enhance security. Users must use these tools effectively.
A strong cloud security strategy can prevent data breaches. It also helps in maintaining compliance with regulations. Let’s dive deeper into the importance of cloud security and common threats.
Importance Of Cloud Security
Cloud security is critical for protecting sensitive data. Many businesses store valuable information in the cloud. Without proper security, this data can be compromised.
A breach can lead to financial loss. It can also damage a company’s reputation. Customers trust businesses to keep their data safe. Ensuring cloud security helps maintain this trust.
Cloud security also ensures compliance with regulations. Many industries have strict data protection laws. Failing to comply can result in hefty fines.
Common Threats In The Cloud
There are many threats to cloud security. One common threat is data breaches. Hackers often target cloud environments to steal sensitive information.
Another threat is data loss. This can happen due to accidental deletion or hardware failure. Without proper backups, lost data may be unrecoverable.
Insider threats are also a concern. Employees with access to sensitive data can misuse it. This can be intentional or accidental.
Malware and ransomware attacks can disrupt cloud services. These attacks can encrypt data, making it inaccessible. To avoid these threats, strong security measures are essential.
“`
Identity And Access Management
Identity and Access Management (IAM) is crucial for securing cloud infrastructure. It ensures that only authorized users can access specific resources. Effective IAM prevents unauthorized access and protects sensitive data.
Implementing Strong Authentication
Strong authentication methods are essential. Use multi-factor authentication (MFA) to add an extra layer of security. MFA requires users to provide two or more verification factors. This could include something they know, like a password, and something they have, like a smartphone.
Biometric authentication can also be used. This includes fingerprint scans or facial recognition. These methods make it harder for unauthorized users to gain access. Ensure that passwords are strong and complex. Regularly update and change passwords to prevent breaches.
Role-based Access Control
Role-Based Access Control (RBAC) helps manage user permissions. Assign roles based on job functions. Each role should have specific access rights. This limits access to sensitive information.
Regularly review and update roles. Ensure that users have the correct permissions. Remove access for users who no longer need it. This reduces the risk of internal threats.
Use the principle of least privilege. Give users the minimum access needed to perform their jobs. This minimizes potential damage from compromised accounts.
Data Protection Strategies
Implementing robust data protection strategies is crucial for securing your cloud infrastructure. These strategies help prevent unauthorized access, data breaches, and data loss. Let’s explore some effective methods to safeguard your sensitive information.
Encryption Methods
Encryption is essential for protecting your data from unauthorized access. It converts readable data into an unreadable format, ensuring privacy.
- Symmetric Encryption: This method uses a single key for both encryption and decryption. It’s faster but requires secure key management.
- Asymmetric Encryption: This method uses a pair of keys – one public and one private. It provides higher security but is slower.
- End-to-End Encryption: This ensures data is encrypted on the sender’s device and only decrypted on the receiver’s device.
Use strong algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) for robust security.
Data Loss Prevention
Data Loss Prevention (DLP) tools help prevent data breaches and accidental data leaks. They monitor, detect, and block sensitive data transfers.
| Method | Description |
|---|---|
| Network DLP: | Monitors data in transit across the network. |
| Endpoint DLP: | Protects data on end-user devices. |
| Storage DLP: | Secures data at rest in storage systems. |
Implementing DLP policies and classifying sensitive data can help in identifying and protecting critical information.
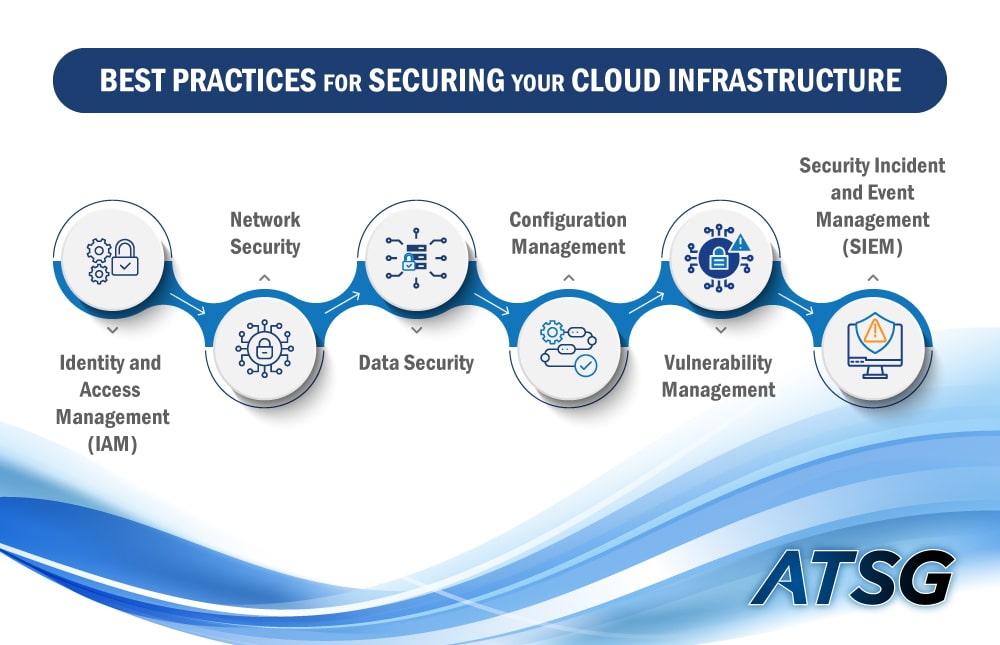
Credit: www.atsg.net
Network Security Measures
Securing your cloud infrastructure is crucial. Network security measures are vital to protect your cloud resources from unauthorized access and cyber threats. Implementing strong network security practices can help ensure your data remains safe and your services run smoothly.
Securing Cloud Networks
Securing cloud networks involves several critical steps. These steps help protect the integrity, confidentiality, and availability of your data. Here are some key practices:
- Network Segmentation: Divide your network into smaller segments. This reduces the attack surface.
- Access Controls: Implement strict access controls. Ensure only authorized users can access sensitive data.
- Encryption: Use encryption for data at rest and in transit. This prevents data breaches.
Firewall Configuration
Proper firewall configuration is essential. Firewalls act as a barrier between your network and potential threats. Here are some best practices:
- Default Deny: Set your firewall to deny all traffic by default. Allow only necessary traffic.
- Regular Updates: Keep your firewall software up to date. This helps protect against new threats.
- Monitor Logs: Regularly monitor your firewall logs. Look for suspicious activity.
By following these network security measures, you can significantly enhance the security of your cloud infrastructure. Stay vigilant and regularly review your security practices.
Monitoring And Logging
Monitoring and logging are crucial for securing your cloud infrastructure. They help you detect, understand, and respond to security incidents. Proper monitoring can identify potential threats in real-time. Effective logging provides a trail of evidence for investigations. Both practices are essential for maintaining a secure cloud environment.
Continuous Monitoring
Continuous monitoring means keeping an eye on your cloud infrastructure 24/7. It involves tracking all activities and changes within the system. Regular checks can help detect unusual behavior early. Use automated tools to ensure no part of your system goes unmonitored. Automated alerts can notify you immediately about potential threats.
Log Management
Log management involves collecting and analyzing log data. Logs record every action taken within your cloud infrastructure. They provide valuable insights into user activities and system changes. Proper log management helps in identifying security breaches. It also aids in compliance with regulatory requirements.
Ensure logs are stored securely and are easily accessible. Use log analysis tools to sift through large volumes of data quickly. Regularly review logs to spot any anomalies or suspicious activities. Properly managed logs can be a powerful tool in your security arsenal.

Credit: shiftasia.com
Compliance And Governance
Ensuring compliance and governance is critical for securing your cloud infrastructure. These practices help you adhere to regulatory standards and maintain control over your data. Effective compliance and governance strategies protect your organization from legal issues and security breaches.
Regulatory Requirements
Understanding regulatory requirements is the first step. Different industries have different standards. For example, healthcare must comply with HIPAA, while financial services follow PCI DSS guidelines.
| Industry | Regulatory Standard |
|---|---|
| Healthcare | HIPAA |
| Financial Services | PCI DSS |
| Education | FERPA |
Always stay updated with the latest regulations. Regular audits help ensure compliance. Ignoring regulatory requirements can lead to hefty fines and reputational damage.
Policy Enforcement
Enforcing policies is key to maintaining governance. Create clear policies for data access, storage, and sharing. Use automated tools to enforce these policies.
- Automated monitoring tools
- Access control systems
- Regular training for employees
Regularly review and update your policies. Ensure all employees understand and follow them. Policy enforcement reduces the risk of data breaches and ensures compliance with regulations.
Incident Response Planning
Incident response planning is crucial for cloud security. Ensure quick detection and response to threats. Regularly update and test your plan.
Incident response planning is crucial for securing your cloud infrastructure. It’s about preparing for potential security breaches and minimizing damage. A well-designed plan helps your team act quickly and effectively during an incident.
Developing A Response Plan
Start by identifying all possible threats to your cloud infrastructure. Create a detailed list of vulnerabilities. Next, define roles and responsibilities for your team. Each member should know their specific duties. This ensures a coordinated response.
Document step-by-step procedures for various incidents. Include contact information for key personnel. Make sure your team knows how to reach each other quickly. Regular training and drills are essential. They help your team stay sharp and ready.
Post-incident Analysis
After an incident, conduct a thorough review. Identify what went wrong and why. Was there a gap in your security measures? Did your team follow the plan correctly?
Analyze the effectiveness of your response. Determine how quickly the team reacted. Look for areas of improvement. Update your response plan based on these findings. Regular reviews and updates keep your plan effective.
Remember, a strong incident response plan is key to cloud security. Prepare, act, and learn from each incident. This cycle helps protect your infrastructure.
“`
Best Practices For Cloud Security
Implementing robust access controls and encryption techniques is essential for cloud security. Regularly updating security policies and conducting audits helps protect your cloud infrastructure.
Securing your cloud infrastructure is essential. Cloud security keeps your data safe and your systems running smoothly. Without proper security, your data is at risk. Following best practices helps prevent breaches and ensures compliance.
Regular Security Audits
Conduct regular security audits. Audits identify vulnerabilities and security gaps. They help you stay ahead of potential threats. Use automated tools for continuous monitoring. Ensure you have a process to review audit findings. Address issues promptly.
Employee Training
Train employees on cloud security practices. Make sure they know the importance of strong passwords. Teach them to recognize phishing attempts. Regular training sessions keep security fresh in their minds. Create a culture of security awareness. Encourage reporting of suspicious activities.
“`
Future Trends In Cloud Security
The future of cloud security is evolving rapidly. New technologies and methodologies are being developed to protect data and systems. With the rise of cloud computing, security becomes even more critical. Let’s explore some of the future trends in cloud security.
Ai And Machine Learning
AI and machine learning are transforming cloud security. These technologies can analyze vast amounts of data quickly. They identify patterns and detect anomalies. This helps in predicting potential threats before they occur. AI can also automate responses to security incidents. This reduces the time to mitigate risks.
Zero Trust Architecture
Zero Trust Architecture is gaining popularity. It assumes that threats can be both external and internal. This approach requires strict identity verification. Every person and device must be verified, regardless of their location. Zero Trust limits access to only necessary resources. It minimizes the risk of unauthorized access.
Adopting these trends can significantly enhance your cloud security. Staying updated with these practices ensures a more secure cloud infrastructure.

Credit: www.esecurityplanet.com
Frequently Asked Questions
How Do I Secure My Cloud Infrastructure?
Securing your cloud infrastructure involves using strong access controls, encryption, and monitoring. Regularly update and patch your systems. Use multi-factor authentication.
What Are Cloud Security Best Practices?
Cloud security best practices include using strong passwords, encrypting data, and regularly updating software. Implement network security measures and monitor for suspicious activity.
Why Is Cloud Security Important?
Cloud security is important to protect sensitive data from breaches and unauthorized access. It ensures data privacy and compliance with regulations.
How Can I Improve Cloud Security?
Improve cloud security by using firewalls, encrypting data, and implementing strong access controls. Regularly update and patch systems.
Conclusion
Securing your cloud infrastructure is crucial for protecting your data. Follow best practices consistently to ensure safety. Regular updates and monitoring help prevent threats. Educate your team on security protocols. Use strong passwords and multi-factor authentication. Back up data regularly for quick recovery.
With these steps, you can keep your cloud environment secure. Stay proactive and vigilant. Your efforts will pay off in maintaining a safe and reliable cloud infrastructure.